Ronin is a side chain of the Ethereum Network which is operated by the famous P2E game; Axie Infinity. It is a network secured by 9 validators. As with most projects out there, if at least 55% of the validators come together to authorize a transaction, it would be successful. In this case, just 5 out of the 9 validators was needed to hack the network.
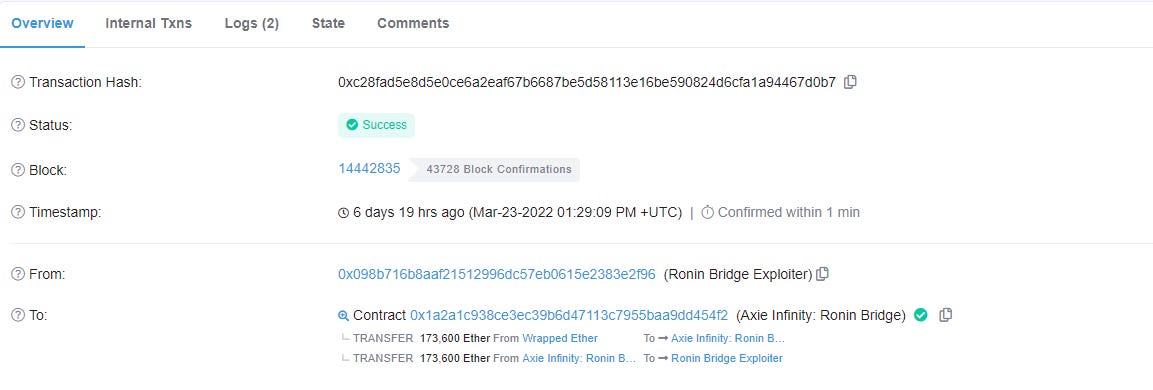
The hackers didn’t just randomly get access to the validators. The hackers went through some complicated maneuvering and got access to the system operating 4 of the nodes that secured the funds on the ronin bridge. Then, they managed to find a bug that revealed another node. That extra node was just enough to reach 50% consensus and with that, they stole all the bridged Ether and USDC. The ronin bridge was exploited for 25.5M USDC and 173,600 Ether. This makes it the topmost hack in the entire history of crypto.
This hack was carried out on the 23rd of March 2022 but was only noticed 6 days later on the 29th. The whole money was drained from the bridge in two transactions.
This attack can be traced back to November 2021 when the Sky Mavis requested help from the Axie DAO to distribute free transactions due to an immense user load and was allowed to do so. However, this was discontinued in December 2021 but the allowlist wasn’t revoked. This was the tiny window the hackers needed to make the theft. Once they got access to the Sky Mavis systems, they were then able to get the signature from the Axie DAO validator by abusing the gas-free RPC that was initiated on November 2021.
This Ronin bridge hack is very different from the normal and rampant bridge hacks where smart contract bugs give hackers access. This ronin hack was way more sophisticated as it was a hack of private keys in a multi-key security setup. It happened through vulnerabilities in key management & off-chain infrastructure and since this isn’t a smart contract root cause, there is really no public trace of what went wrong.
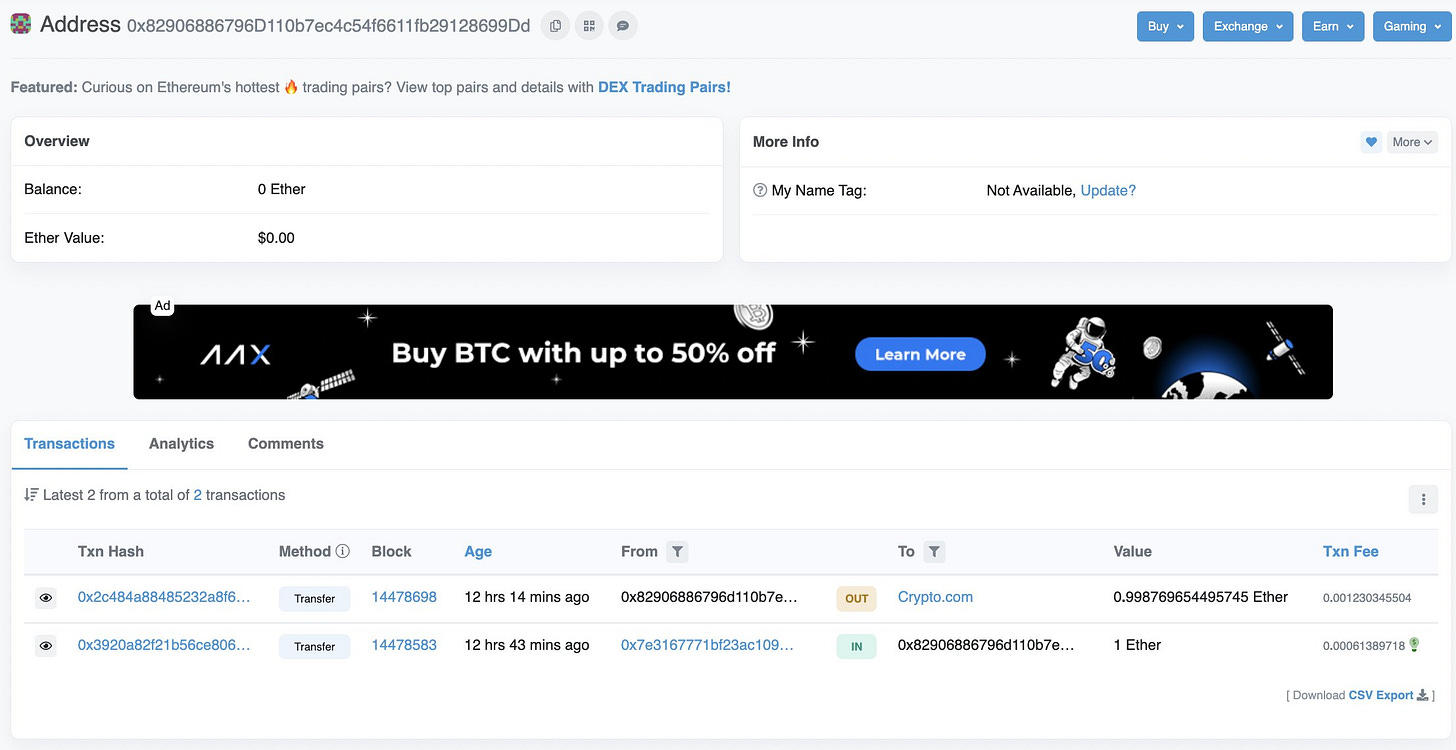
Since this hack happened 7 days ago, the hacker has literally been sending some of the stolen Ether to FTX and Crypto.com.
If this is just psyops or a cashout plan, no one knows but Ronin is now working with SBF and government agencies to recover the funds.
It is now clear that these hacks are getting more sophisticated as the days go by, and they’re also getting very much devastating. I believe this trend would continue as long as multisig bridges scale and liquidity spreads through chains. We need better bridges as these are massive honeypots for hackers. The Ronin bridge was a validator-based bridge and had a fatal assumption that a majority of the keys couldn’t be compromised. We see how that went right??
No single entity should be running a significant amount of nodes in any network. In the the ronin hack, the 5 compromised nodes was basically one! (sky mavis)
Projects such as Axie Infinity should learn to invest in multiple client implementations and client diversity
Keep steady alerts on chain/bridge balance. If balance goes below a certain threshold, alerts should ring!!!
Introduce withdrawal delay depending on the size of the transaction. This would force would-be hackers to break down the withdrawal transaction into small quantities but would trigger the alert system.
Make a system where latency is proportional to size of withdrawal.
Conclusion:
This is a massive test on decentralization and privacy in crypto as we know it. Hacks such as this gets government attention and trust me, this isn’t the type of attention that we need. This is negative PR. Is this the industry that wants to secure more than $5 trillion in global assets? Some persons might argue that it is the cost of doing transaction on-chain and code is key but does this mean theft is now legal and that anyone can just wake up one day and decide that he/she should just a attack a project because code is law? Now, imagine if you were the one that was at the receiving end of such attacks. We all know what became of Mark Cuban after the $2b crash of Iron finance. As Miko Matsumura says, we should not allow our primitive ideas on game theory and laissez faire economics to cloud our thoughts. We should consider the primacy of consent. For ways to combat such thefts, i’ll just link you guys up to ideas made by the gigabrains like hasufl, Emin Gün Sirer, CryptoDragonite.
There’s not much possibilities after this hack. It’s either the hacker gets sloppy and gets caught, the stolen funds is just blacklisted and essentially burned from supply until the hacker is caught (somewhat bullish scenario innit?) or Ronin is forced to buy back the lost funds to compensate customers like what happened during the solana wormhole hack. If anyone want to dig further, here’s the link to the address holding the stolen funds.